Table of contents
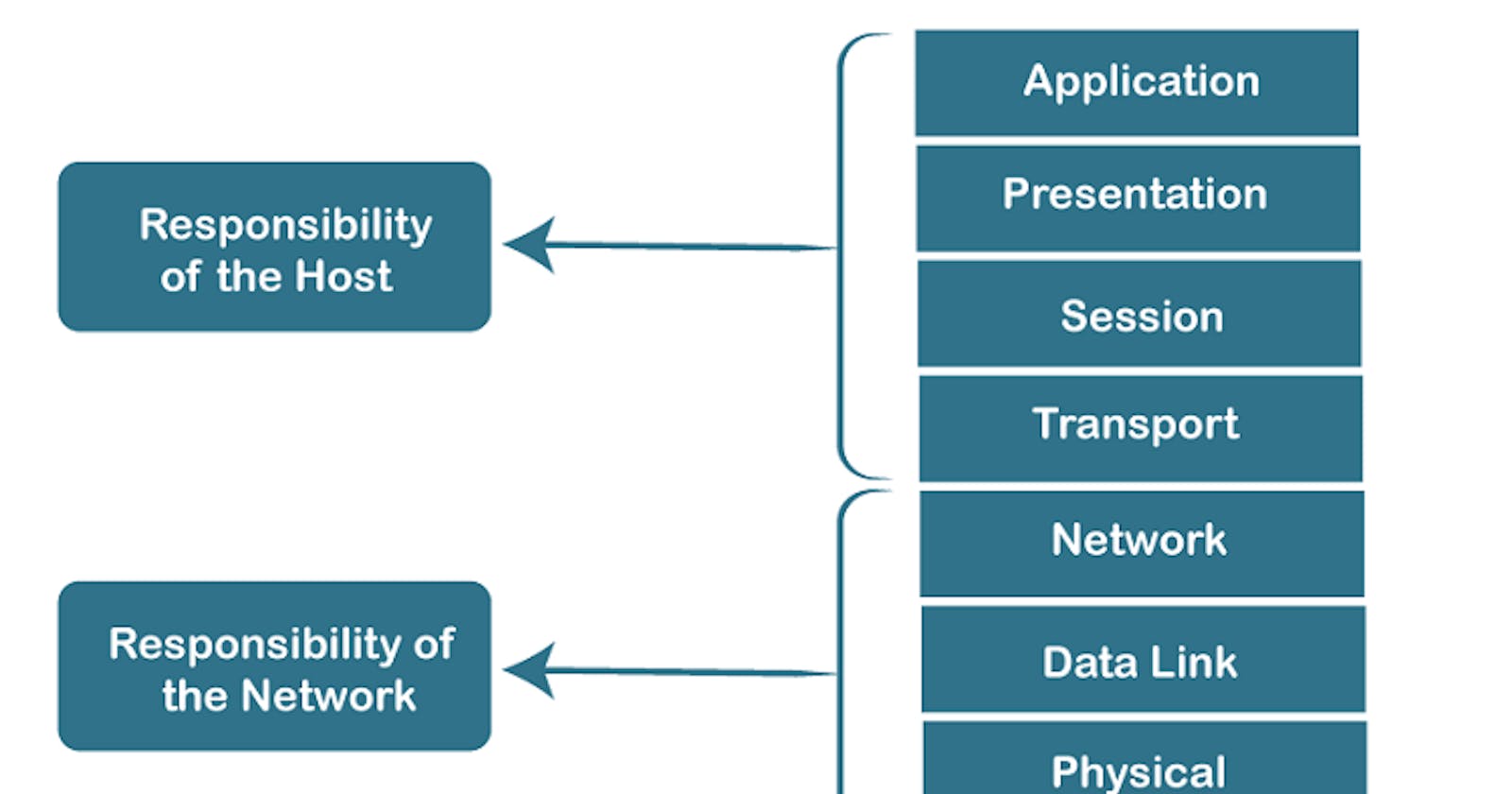
The OSI Model is a basic and conceptual framework that standardizes the functions of a telecommunications or computing system into seven distinct layers. Each layer is responsible for a specific aspect of network communication, creating a structured approach to understanding and implementing network protocols.
These layers, from top to bottom, are:
Application Layer
- Insight: This is the topmost layer that interacts directly with end-users or applications and provides various network services. Application layer protocols include HTTP (Hypertext Transfer Protocol) and FTP (File Transfer Protocol).
Example: When you use a web browser to access a website, application layer protocols like HTTP or HTTPS enable communication between your browser and the web server, allowing you to request and view web pages.
Role in the Backend Development: Backend developers frequently work in the Application Layer, where they design and implement web services, APIs, and other networked software. Understanding application layer protocols is essential for creating user-facing and backend services.
Presentation Layer:
Insight: The presentation layer handles data translation, encryption, and compression to ensure the data is in a usable format.
Example: When data such as arrays, JSON, or tokens are sent from the server to the client, this layer handles the encryption of such data for safe transmission.
Session Layer:
Insight: This layer is responsible for managing sessions or connections between devices and maintaining the conversation context.
Example: In a video conference call, the session layer ensures that your audio and video data stays synchronized between your device and the remote participants throughout the call.
Transport Layer:
Insight: Think of the transport layer as ensuring a reliable connection between two devices and managing the size and flow of data.
Example: When you download a large file from a server, the transport layer (e.g., TCP) ensures that all parts of the file arrive intact and in the correct order, even if some packets are lost or arrive out of order.
Role in Backend Development: Backend developers often work with transport layer protocols like TCP and UDP when developing applications and services. Understanding these protocols is essential for optimizing data transmission and ensuring reliability.
Network Layer:
Insight: The network layer is like a postal service, determining how data gets from one network to another using logical addressing (IP addresses).
Example: When you type a website's URL into your browser, the network layer handles routing your request through various routers on the internet until it reaches the web server's IP address.
Data Link Layer:
Insight: This layer manages communication on the same network and ensures data integrity within that network.
Example: Ethernet is a data link layer protocol. When you connect your computer to a router with an Ethernet cable, this layer ensures that data packets are correctly sent and received within your local network.
Physical Layer:
Insight: Think of the physical layer as the actual hardware components that enable data transmission, such as cables, switches, and network cards.
Example: When connecting to the internet via Wi-Fi, you're relying on physical layer components like the Wi-Fi router, antennas, and the radio waves that transmit data between your device and the router.
Observations:
Below are not part of the article, but just findings and my observations while studying this chapter.
Observation 1
An example of a POST request being sent to an HTTPS webpage and how it interacts with each layer of the OSI model:
Scenario: Imagine you're using a web browser to submit a contact form on a secure website (e.g., submitting a message to a customer support team). The website uses HTTPS to encrypt the data transmission for security.
Findings:
1. Physical Layer:
- Your computer communicates with the web server over a physical medium, which could be Ethernet if you're connected via cable or Wi-Fi if you're on a wireless network. This layer deals with the transmission of raw binary data (0s and 1s) over the physical medium.
2. Data Link Layer:
If you're on Wi-Fi, this layer handles things like Wi-Fi signal modulation and MAC addresses. If you're on Ethernet, it deals with Ethernet frames.
Your computer sends an Ethernet frame or Wi-Fi packet containing the data to your router or access point.
3. Network Layer:
The data packet is then routed through your local network, typically using IP (Internet Protocol) addresses. Your router determines the best path to the web server's IP address.
The packet is forwarded to your Internet Service Provider (ISP) through various network routers.
4. Transport Layer:
Your computer uses the transport layer to establish a connection to the web server. It uses the HTTPS protocol (typically over TCP, which ensures reliability).
A TCP connection is established between your computer's IP address and the web server's IP address.
5. Session Layer:
The session layer manages the session or connection between your computer and the web server. It ensures that the communication remains synchronized.
A session is established for the duration of your interaction with the web server.
6. Presentation Layer:
In this layer, your web browser may handle data translation (e.g., converting text and images into a format that can be displayed).
The data, including the contents of the contact form, is prepared for transmission.
7. Application Layer:
At the top layer, your web browser creates an HTTP POST request. This request includes the form data you entered (e.g., name, email, message) and the URL of the secure website (e.g.,
https://example.com/contact).The HTTP POST request is encrypted using the HTTPS protocol. The encryption ensures that your data remains confidential and secure during transmission.
The request is then sent to the web server over the established TCP connection
Observation 2.
Both RESTful APIs and HTTP, which operate at the Application Layer in the OSI model, are stateless. What does statelessness means in each context and If they are connected how are they connected.
Findings:
1. Stateless REST APIs:
Statelessness: REST (Representational State Transfer) is an architectural style for designing networked applications. In a RESTful API, statelessness means that each HTTP request from a client to a server must contain all the information needed to understand and fulfill the request. The server does not maintain any information about the client's state between requests.
Example: Consider a simple RESTful API for a blog. When a client requests a list of blog posts, it sends an HTTP GET request to a specific URL, such as
https://example.com/api/posts. The server processes the request based solely on the information in the request itself, without relying on any previous requests or client state.
2. Stateless HTTP in the OSI Model:
Statelessness: In the OSI model, HTTP operates at the Application Layer, which is inherently stateless. Each HTTP request/response pair is independent and does not carry any information about the client's previous interactions with the server. The server processes each request in isolation, without maintaining any session or context between requests.
Example: When you access a web page using your web browser, each click on a link or submission of a form sends a new HTTP request to the server. The server processes each request based solely on the information in that request, without any knowledge of your previous interactions with the website.
Connection and Significance:
The connection between stateless REST APIs and stateless HTTP is that RESTful APIs are typically built on top of the HTTP protocol. REST leverages the statelessness of HTTP to create scalable and loosely coupled services.
The statelessness of HTTP allows for horizontal scalability, as servers can process requests independently without needing to share session information. This is crucial for building distributed and scalable web applications.
Advantages:
Stateless architectures are easy to scale because any server in a cluster can handle any client request without relying on session-specific data.
Stateless systems are more fault-tolerant, as the failure of one server does not impact the state or session of a client.
Stateless systems are generally easier to cache and optimize for performance since each request can be processed independently.